The Cyber Battleground’s Evolving Nature
As the development of innovative technologies, including security tools, continues to grow, the threat landscape is also not stable. New methods of attacking users’ information in cyberspace are coming into play every time. Modern cyber warfare does not change its “battlefield,” but in the current conditions of the digital age, we can only talk about active confrontation, not the complete eradication of enemy threats.
The Anatomy of Modern Cyber Threats
Malware evolution in such a way as to find new methods to attack users online every time. For example, numerous threat actors now have the following main characteristics:
● Increasing the number to put a heavy load on the system;
● Use of artificial intelligence for fast and sophisticated cyberattacks;
● Targeting and anonymity.
In general, modern cyberattacks often use the concept of sophisticated attacks, which makes them more dangerous.
Top 5 Prevailing Cybersecurity Threats
The top 5 main cyber threats include:
- Phishing and Smishing. The purpose of phishing attacks is to steal confidential data (logins, credit card passwords, etc.).
- Malware. Such ransomware can block the normal operation of the device and demand a financial ransom.
- IoT vulnerabilities. These threats relate to the weaknesses of all IoT devices. As a result, it can lead to security breaches, confidential data leakage, and unauthorized access to IoT devices.
- DDoS. The main characteristics are spam traffic, resource allocation (i.e., an attack from different computers), and server resource overload.
- Man-in-the-middle. A type of cyberattack aimed at intercepting and changing communication between two objects without their consent. In this way, the attacker seems to eavesdrop on all the information and can manipulate the data received.
The purpose of each of the described cyberattacks may be different, but any third-party aggressive action on the system can harm the user: both in terms of information leakage and actual system overload.
The Silent Threats: Less Known but Equally Damaging
All cyber threats have their level of danger. Even lesser-known “silent” threats can cause great damage. They include insider threats that compromise the company’s security. They can be intentional or unintentional.
Cryptojacking can also be dangerous. This is the process of illegal cryptocurrency mining. Cryptojackers use mining programs to mine currency. This is a significant hidden danger for a large audience of cryptocurrency users.
Another dangerous cyber threat is supply chain attacks. They focus on hacking into infrastructure and resources that are considered to be secure. The main goal is to damage systems that are part of the supply chain.
Consequences of Underestimating Cyber Threats
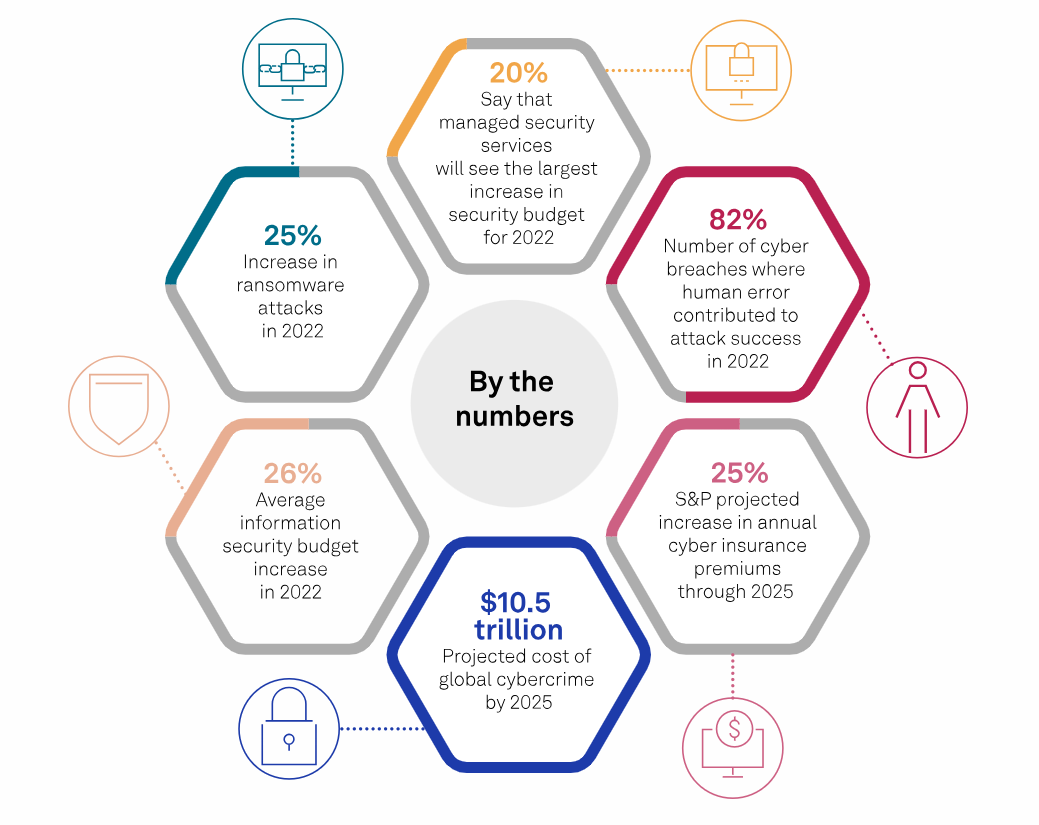
The Verizon DBIR report shows a “25% increase in ransomware attacks in 2022”. Therefore, last year, numerous companies did not take care of their full protection against possible cyber threats.
Businesses that don’t prioritize cybersecurity may experience undesirable results:
● data breaches;
● financial loss due to theft;
● reputation damage. After all, any external influence can negatively affect the company’s reputation.
In addition, cyberattacks violate the company’s confidentiality, which can lead to the public disclosure of highly confidential data.
A Quick Peek into the Future: Predicted Cyber Threats
In updated statistics, the AAG portal reports that 39% of UK companies were cyber-attacked in 2022, and in America, more than 53.35 million citizens were impacted by cybercrime (and this is for the first half of 2022). The AAG notes that phishing is a popular method of attack.
Looking to the future, there is a high probability that phishing will remain the most popular method for cyberattacks. Instead, attackers may begin to use AI-driven attacks to have a more powerful impact on users’ systems.
However, in the future, attackers may start to use deepfake threats more actively to manipulate the audience, as well as quantum hacking of cryptographic systems.
The Imperative of Proactive Cyber Defense
Given the active digitalization of all industries, vigilant defense is a necessary component of staying safe online. At the same time, our cyber readiness should be constantly improving, not stagnant.
The cyber threat is a changing and impermanent concept. To properly confront current problems, society must use adaptive security to make it more likely to avoid undesirable consequences.
